Tuesday Sweep: 11 July 2017
Welcome to your weekly reminder to back up your data, update software and otherwise pay attention to your digital environment. (Oh, and to come to the CRASH Space meeting…)
Jump in Here
- Welcome. If you haven’t been following along, it’s okay. You’re not behind, you’re just where you are.
- I highly recommend the coach tool at the Crash Override Network has a great step by step break down for many of the same introductory steps we did here.
- Feeling more ambitious? Review the list of OneThing articles and pick one to catch up on.
Sweep
The basics.
- Updated software recently? Pick a new device to check on today.
- Backups still up and running? When was the last time you made a clean disk image? Here’s a new great article on how to design a backup system.
- App and Password Gardening: Delete a low quality app from your phone or delete an account that you don’t need that doesn’t make you happy. Digital cruft builds up. Delete it. If you’re keeping it, can you move the password to your password manager (delete it from everywhere else) and add two factor authentication?
- Move to offline archive & delete your histories where you can find them.
- Double check privacy settings on your phone, social media accounts. The folks running the companies can change the TOS and add “features” before you notice them.
Learn: Weekly Round Up
Where do you scan for news?
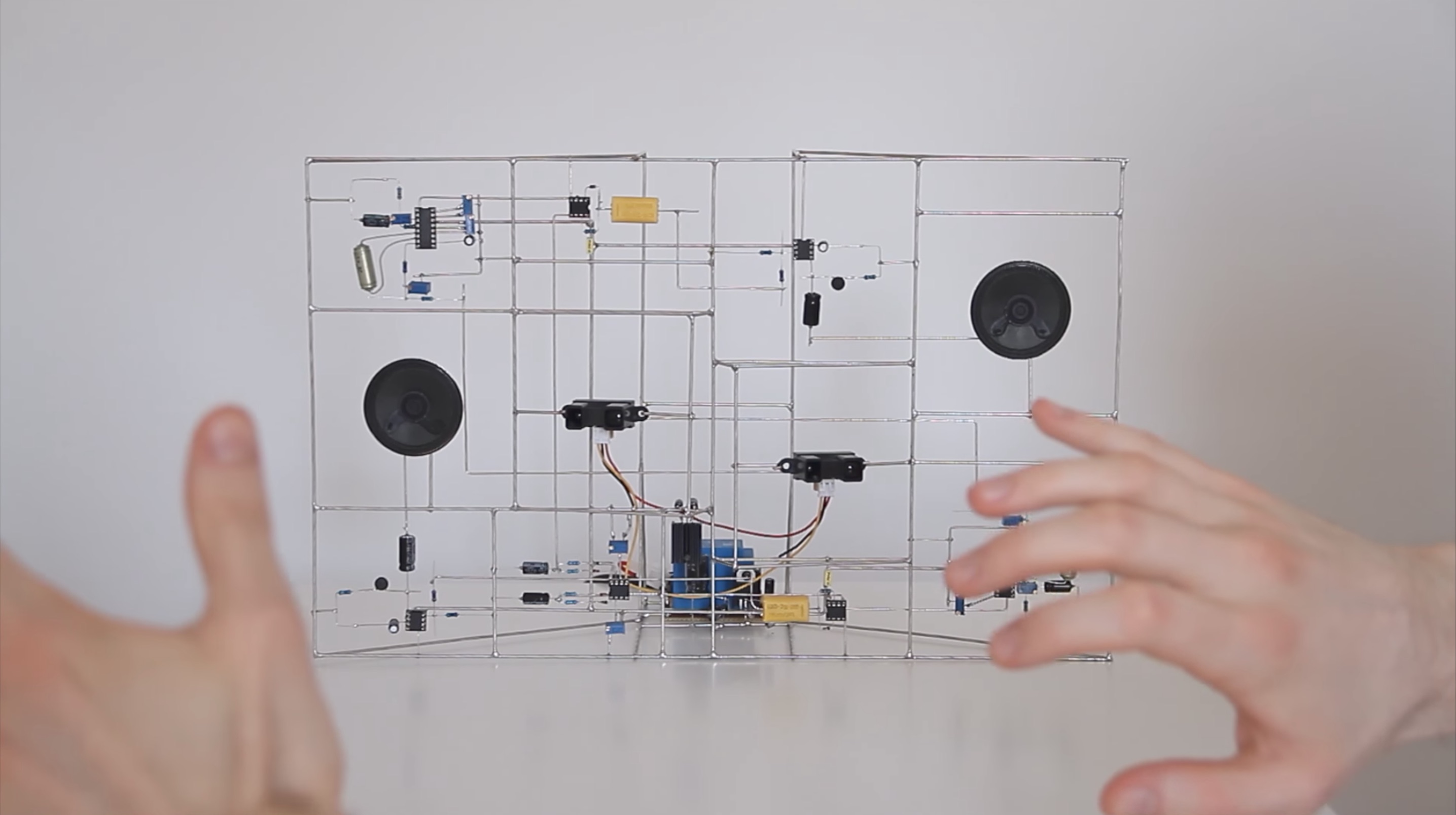
- Eirik Brandal makes instruments from structural circuits. Wow. So cool, with an aesthetic that reminds me of Duchamp a little. Watch the video (via BoingBoing again!)
- EFF “Who has your back?” List is out for 2017. This annual list reviews several large companies based on each company’s policies on how, when and whether to comply with government data request. A shout out to the companies that aced this particular test: Adobe, Credo, Dropbox, Lyft, Pinterest, Sonic, Uber, Wickr, and WordPress. I highly recommend not just scanning the pretty chart, but reading at least the executive summary as well.
- Want to perform a billion billion calculations per second? Then you want an exscale super computer. The US has just gotten serious about being first again. The New Yorker, of all places, had an interesting discussion about what massive computing power means in the cryptoworld using Quantum Computing as the bugbear. TL;DR? IEEE puts it in the headline “Quantum Computer Comes Closer to Cracking RSA Encryption,” but I like the Quartz media article better because it quotes Poe.
- Speaking of an Arms Race. I’ll admit I’ve been low level freaking out ever since I watched Adobe unveiled VoCo by making Keegan-Michael Key’s voice talk about making out with Jordan Peele. I’m glad that the folks at Wired have given themselves leave to freaked out the potential for forgeries, (via Schneier) too. If fake news is bad now… WHEW. We’re in for it. Time to update all those guides on how to assess a primary source… That said, humanity did live in a time BEFORE video was widely available, and this time it wasn’t that long ago. We can at least forward to the increased quality in video/AR games.
- I missed writing much about NotPetya, and its motives, but apparently, once again, it could have been avoided by keeping updated. That said, many firms have legacy software they’ve custom rolled at great expense and honestly don’t know what the consequences will be for updating. If this is you or someone you love, try out Wine “a compatibility layer capable of running Windows applications on several POSIX-compliant operating systems”. In other words, you can run .exe files directly without launching an emulator. If your CXO’s like paying for things try the commercial version CrossOver which purportedly takes the some of the pain out of the equation of configuring Wine correctly. You can keep your Linux up-to-date without harming the ability to keep running the old software running on that old hardware.
- This all said, Jake Williams had an excellent point in the SANS Newsletter 54 “Infosec basics like principles of least privilege would have done more to protect networks [from NotPetya] more than disabling SMB1.” That Phrase “Least Privlege” was coined in a 1975 paper by J.H. Saltzer and M.D. Schroeder called ‘Basic Principles of Information Protection’ I’m squarly in the camp that security is a process, not a product, and discussions of technologies should not be at the exclusion of design patterns. So I’m just going to leave some links here, partially for my own reference.
- ‘Basic Principles of Information Protection’ (As mentioned)
- Indiana University Information Security Best Practices
- US-CERT legacy page “Build Security In” and new, less catchily named site “Cyber Security Engineering“
- Open Web Application Security Project‘s Wiki Category “Principles”
Reflect
Feeling dumb or stupid about how not-l33t you are? Angsting over some silly thing you “know better than to do.” Stop. That isn’t useful. Regret is only of use if it prompts an actual change in behavior. Maybe it’s NOT you that sucks. Could be it’s the technology and you could come up with a fix that would help lots of people. Look forward and make a plan.
Engage
We are a community. You are a welcome part of it.