One Thing To Do Today: Threat Model Part 3, Map The Ecosystem
I’m the weirdo that loved diagraming sentences, so this next part makes me nerdily happy. Time to take one of the “assets” from day one and map out the ecosystem that information moves around. For an example lets take location data.
For me, at this moment, a leak of my location data falls into the high threat, medium risk category. When I look at the list of threat actors I want to make personas for, they typically want money, attention, passwords and computing power, not access to my physical location. So probability feels low. That said if someone with malicious or even mischievous intent can know where I am with any degree of certainty, they could end up doing real harm to my person. This sets potential impact at high. So even though the likelihood of someone targeting my personal location habits is pretty darn low for me, the consequences could devastate. So we start here.
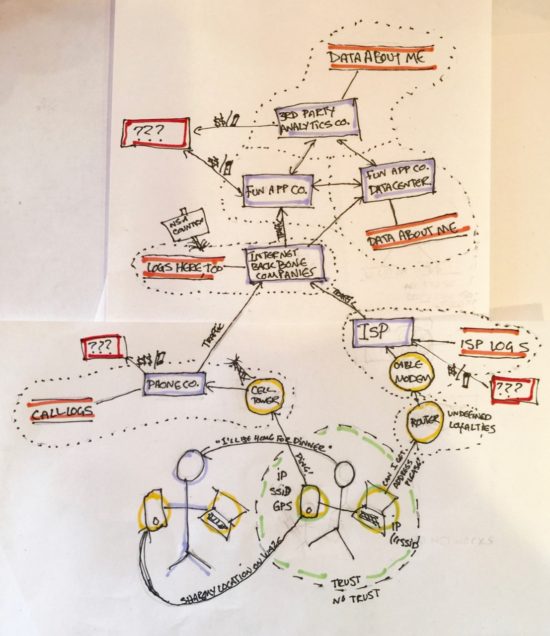
Typical threat model diagrams represent corporate or application systems. More useful to me will be a simplified representation of the basic places my location information passes through and gets kept. Lets go through it from inside out.
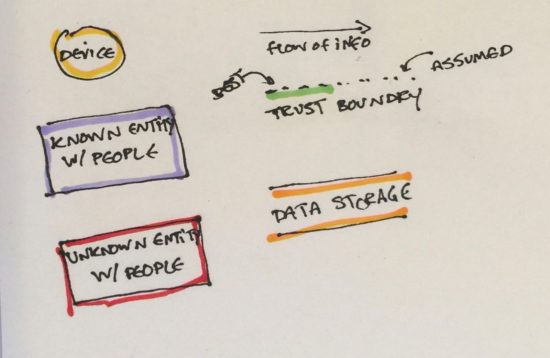
Inside the Circle of Trust, but not yet trustworthy
Items under ones own physical control fall inside the circle of trust. That’s it. Technically, if an item or data packet goes outside of this circle at any time, it’s no longer 100% reliable and must be recertified. I tired to put my husband inside this circle. Backend system design background that he has, he laughed and said no. If he starts calling me Allsion I’ll start to worry, but he has a point. There’s no controlling what precautions friends and family do or do not take.
- My phone
- Local to machine: GPS, What WiFi network its connected to
- Network Info: Cell tower triangulation data, IP address
- My computer
- Local to machine: If it isn’t portable, when it goes on and off is data about my location, WiFi network info
- Network Info: IP address
- Me
- Network Info: Who have I told, called/contacted from this location, what social media have I posted from this location
- Misc Other
- A car with GPS
- Health tracker with GPS
- Home IoT devices that turn on and off based on whether or not you’re there (thermostat, smart TV)
Immediate Connections
The first hop out to the internet, these items help personal items locate themselves, but they also pass that information upstream.
- Router – If your in your own home the router can probably be inside the circle of trust once it’s been properly configured. The remote-updating options made me put the cable modem up a level still.
- Cell Tower – Doesn’t belong to you, does not deserve trust.
- The Sweetheart Tweeting Next to You – Sigh. At least mine knows how to turn off location data.
First Corporate Layer
- Internet Service Provider- Gatekeeper from local position to the internet at large via telephone, cable or fiber network that they may or may not own themselves. Cable modems can typically be controlled and updated remotely by this company, but you have physical control. Affiliation remains mushy.
- Cellular Network Provider – Gatekeeper from local position to the internet using cell tower infrastructure. Again the carrier may or may not own the hardware. They’re definitely tracking you and selling the data.
“The Internet”
ISPs funnel traffic to central “backbones.” The evolution of this infrastructure has some fascinating twists. News that the NSA had planted brain suckers at some of the major hubs moved organizations to action, but everything still goes through them. Ideas for moving away from this style of centralization have a lot of appeal, but not a lot of unified traction… yet. This won’t be one place. To get a real sense of all the places your traffic will go, learn how to use a traceroute.
Second Corporate Layer
So lets say I have some game I like to play on my phone, lets call it GokémonPo. Between GPS and detecting WiFi networks, my location is in their hands real time. This can then get stored in their databases, along with other identifying information to sell at a later time. Many “free” apps make their money off of selling data you may not even know they collect. They may be contracting with a third party analytics company. They likely don’t own their own server hardware. There will be varying amounts of trust between the companies involved in this part of the ecosystem.
Who the Hell Knows
Once these companies sell or otherwise hand off data, no telling what happens with it. We might make some guesses, though.
Next Steps
Now with a diagram in our hot little hands we get to cos-play as threat actors and comb for vulnerabilities. That, however, will have to wait for Wednesday since tomorrow is sweep day. I’ve got so many hoodies. It’s going to be fun.

Pingback: One Thing To Do Today: Threat Model 4, What the Ulitmate Threat Actor Sees