One Thing To Do Today: Threat Model 4, What the Ulitmate Threat Actor Sees
So now we look at our diagram as if we were one of our threat actor personas. To do things right, real data, not just cave shadows, should be putting the flesh on the bones of our persona. I don’t have data I consider good enough at my finger tips, so I’m going full seasonal.
Persona
Aliases: St. Nicholas, Santa Claus, Kris Kringle, Father Christmas, Sinterklaas
Handels: santac, stnk, elfinat0r, nullGift, claws
Locations: North Pole
Gender: male
Age: 1,746
Education: autodidact
Sources of Income: Suspected day job as VP of operations for a toy company, may also dabble in blackmail of naughty list.
Motivations: To find out if targets are Naughty or Nice.
Fears: Honestly more worried about putting a nice person on the naughty list than the reverse, and agonizes over the fact that accidents happen. Also concerned about gift delivery mixups. In recent years these fears have made our threat actor less active, preferring instead a more symbolic role.
Known strengths: Santa Claus’s major strength is Social Engineering. A convivial sort, people hand over massive amounts of private information with minimal prompting. Those he’s reached display a shocking loyalty, even when the exploits have been revealed. He’s believed to be familiar with many types of supply chain management technologies including those used in real time inventory systems. His age makes him evaluate new technologies with rigor, but will quickly adopt those that prove to be actual improvements. Also known to have significant skills at Breaking and Entering.
Known Weaknesses: A bit of an attention whore. Really enjoys hanging out at malls and parades. Frequently appears in commercials. Will sometimes linger too long over cookies. While happy to hand over toy making to his highly trained workforce, he tends to micromanage the actual List.
Objectives: In recent years Santa has focused on location data. Being where one is supposed to be, when one is supposed to be there, with whom one is supposed to be there with provides a first level sort for “Niceness.”
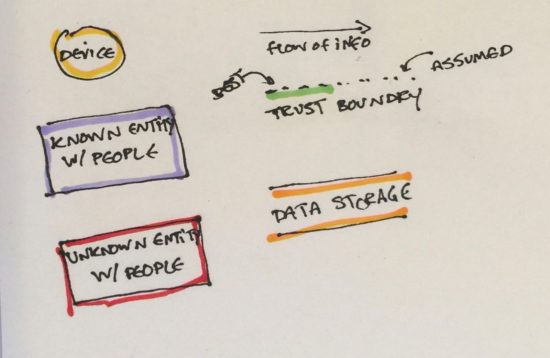
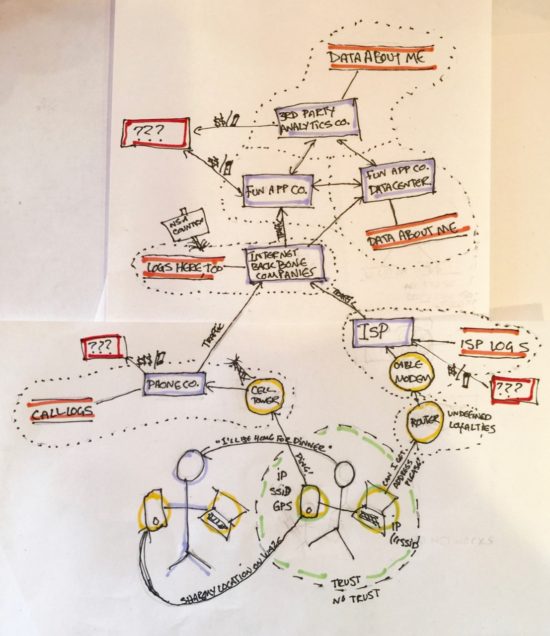
Diagram Being Discussed
Interview
Carlyn on behalf of CRASH Space: Hi Santa, I want to thank you for taking time out of your busy schedule to talk to me.
Santa Claus: [Chuckles, bites cookie]
C: So, here’s this diagram I drew. What do you see?
S: Well, the first thing I see is that you’ve nicely marked in those places I could probably find someone to call. I’m very good at putting people at ease, understanding what they want. This makes easiest for me to call up, chat and get enough information to guess a password. Some times they’ll just hand over logs if I say I’m a researcher or law enforcement. People like to trust me. If it’s on a company’s server and accessible to the employees, I can typically get it.
C: Wow, just like that? And it’s over?
S: Well, it depends. I like approaching companies first because I have a lot of people to track and bulk scrapes of data are the most useful to me. Of those you’ve drawn, lower on my list would be ISP’s and the ones that fall under “Internet Backbone Companies.” IP data is handy to get a general picture, down the line if I’ve managed to figure out a block that means your likely to be home or likely to be at work that’s great, but generally that’s not where I start. I’m trying to find where your home is, where your office is, where you grocery shop, whose generally in those places at that same time… tracking movement patterns. I want geotagged information. Lat-Long data for this step. Once I get through this initial sort, I may go back to an ISP to get information from web traffic, but this first round its all location, location, location.
C: So if not ISPs or backbones, which companies would you approach for this better quality data?
S: So I’m not typically approaching the company as much as I’m approaching someone who works for the company. Someone young, maybe at a first job so they have some angst about adulthood. People with kids. I can be very reassuring. I look like Santa. [Ho Ho Ho]
C: … okay, that’s creepy, but, how do you decide if the company they work for will be useful?
S: Well the phone companies have great data from cell towers. So do any of the companies with an apps that loads a map. But if I can’t get through to the folks at one of those, there are so many mobile app companies these days. Though it would be preferred, I don’t have to get in to one of the telcos.
C: Any mobile app company?
S: Mobile phones have very rich location information available to them. GPS. WiFi chips reading SSIDs. What cell towers are closest. Companies release an app for free or super cheap, to maximize downloads. That limits the number of places I have to call. The companies I look for have a small ratio of employees to install base. Chances are good they’re struggling to keep up with flashier features rather than data security. Some of these places aren’t even using https to retrieve the data.
C: Wait what?
S: Yeah, apps, frequently send data in the clear.
C: Wait, how can you tell?
S: I’ll put a packet sniffer in your stocking. They don’t exactly announce it in the app. But catching data while it travels typically isn’t my approach to start. I’m not spoofing cell phone towers either because at this step I’d need too many of them. I want the bulk data stored in logs at companies.
C: Uh, okay. But didn’t you say the folks with location data are cagey?
S: The people who obviously collect location data can be more suspicious. But depending on your phone, any app can scrape location data. Really, any. I’m talking social media, step trackers, flashlights. Some offer it up via APIs, but if I’m getting really desperate I can pretend to be from a location based ad company. Flashing some revenue is a real encryption dropper. If there even was any.
C: Okay, so app companies that collect location data…
S: Pictures, I look for user uploaded pictures, too. The pictures themselves store the location information.
C: That’s right. In EXIF data
S: Yup, in the EXIF… and if I need to get creative? What else? Okay if I’ve bombed at finding someone at the phone companies, map companies, travel apps and business recommendation sites. I’ve moved on to fitness trackers and social media… people put a lot on social media without much prompting. That’s where I pick up a lot of the information on where people think they’re supposed to be, too. What their image of themselves is, so that really should have been up at the top. No sneakiness required. I can use it to convince someone at a company to talk to me too. Strike up a conversation about a hobby. Pretend to be a friend of a friend. But anyway, if that has failed. I’d try to find a company hoping to cash in on location based advertising and work that angle. So finally I guess that gets us to IoT companies.
C: Why IoT companies? I know they can listen and be creepy, but what do they know about my location?
S: Well location from listening…if it has sound data I can get to, I can drive through a neighborhood in July blasting Christmas music, I have enough elves that I could do some decent coverage. But that’s not what I’d try first. IoT devices live in one place, a toaster isn’t coming on a milk run with you. So if I can get usage logs from an IoToaster company I can when you’re home having breakfast. And if that device gets connected to a known phone that helps me link it to you specifically even better. Oh, and, you’re in LA, most of Los Angeles gets to work via cars, lots of them with GPS of some sort in them these days. Those companies might have a logs, too.
C: So that’s a lot of options. But let’s say for a minute, that you’ve been completely unsuccessful at charming anyone out of passwords or data. What do you then?
S: I’d write my own app or website. Probably a game. I’m still Santa, after all. I’d design it so little present animations would arrive randomly, but what they are would depend on where you are. There’d be notifications so the app wouldn’t need to be on screen for you to get a present. That would make it so people would always leave location sharing on, but it’d seem like a logical reason. Keep the suspicions low. I’d add a trading or sharing component so you’d want to link your phone to other phones in the area. It’d scan for available bluetooth devices in the background for sure. If it’s on WiFi, check what else is on the network. I could locate people who don’t have the app installed that way. Maybe it’s listening for ambient music? To change what presents people get based on the music playing? That’d be a reason to get people to leave the microphone on. People hearing the same sounds will likely be in the same place. I mean, once it is MY app on your phone? And if its FUN? I bet I could even tell people what its for. After all, most people think of themselves as Nice, not doing anything wrong enough to getting coal for. [Looks sad.]
C: Sounds like you’ve given this some thought.
S: Actually that took very little effort. I’ve been at this game a long time.
C: So with all this new data, does making the naughty and nice lists get easier every year?
S: No. As a matter of fact it’s gotten harder.
C: Harder?
S: Listen, I like giving presents. I want people to be worthy of their hearts desire. I’m all about the positive reinforcement. That coal thing, deeply misunderstood. Coal becomes diamond under pressure. I started giving it out as a message of hope to try harder. I hadn’t been hanging out with a lot of kids at the time. You could say my workshop has a bit of a demographics problem. But see, I have a responsibility to make my naughty list as high quality as I can. I really try to put people on it for their own good. But there’s too much data. It’s too easy to get false positives. I mean I thought this one kid was was cheating on his girlfriend with his girlfriend’s best friend… they were planning a surprise party. That was embarrassing. And the algorithms I’m finding to process this data? Whole zip codes or brands of phones are just marked naughty with no other evidence at all. And what about an alcoholic that shows up in a bar? Are they drinking? I can’t tell. Maybe they’re there to keep a friend company who’s had a bad day. What am I supposed to do with that information? It’s worse than useless.
C: So why do you collect it?
S: At first, it was such a rush. I could know everything. I mean. I thought I could. I’m just an elf, but I felt like a god. Like I could really finally get these lists right. Now? I’ve been scaling back on the data collection. Especially since Krumpus has been getting involved. So I’ve been putting in more Mall appearances. Real face to face community work. In the end I think I get a better list that way. If I spend too much time obsessing over catching every naughty person, I’m not making presents. Bringing joy, that’s the real mission.
C: Well, Thank you for taking time to look over this diagram with me Santa. I think we’ll be able to come up with some good ideas from your insights. I really appreciate all the hard work you do. One last question. We’ve been talking mostly about location logs, but if you needed to find out where I was real time, what would you do?
S: That’s easy. You share your location with Tod. Tod will rat you out every time.
C: Wait what??
S: I know all the LED manufacturers.
C: Yup, I guess you would. I suppose that makes sense. Thank you again Santa. Safe travels.
S: Happy Holidays, Carlyn. Good will towards all.


Hey! I would not rat you out to Santa, no matter how good of a deal on RGB LEDs he gives me… well…
Mmmhmmm.
Pingback: One Thing To Do Today: Threat Model 5, How to look for mitigations