One Thing To Do Today: Learn about The Onion Router, Tor
TL;DR Educate yourself before using. If you’re in, download the software, set it up correctly, use it with care. Next steps include donating to an exit node provider or setting up a relay yourself.
I’ve put off talking about Tor because, well, discussing Tor takes nuance. Whether or not you decide to bring Tor into your life on the regular, learning about how it works and how clever folks get around it will sharpen your security mindset. I think even if you think, “I don’t need Tor,” there are vulnerable people in the world who could use the cover of your banal data going over the same network. Using Tor doesn’t make you a criminal, and there are great reasons to do so. Since Tor constantly gets pummeled by folks looking for exploits and is therefore also constantly updated, I thought it important to highlight the date of the information being provided. The links get more in depth down each list, so the top ones may be the only one you need.
Proxies

Getting your head around Tor starts with understanding Proxies. When I think of proxies I think of those glove-box isolation chambers. A proxy lets you handle another website without getting your IP address dirty. That box can also sometimes hold a local copy of a website or file if the person running the proxy predicts a lot people will want to handle it from one location. While going through a proxy(s) can slow web traffic down by adding hops, local caches speed things up. If you’re using StartPage as your search engine, next to each link is the option of going to the page via a “Proxy.” Top Google search results tend to served by proxy by default, so you may be being served from one now without even knowing it. Proxies DO NOT provide encryption. They’re merely call forwarding.
- Video: Proxy, VPN, SmartDNS (BestVPN, 3:10)
- Video: Proxy Server (2011, Greg French, 5:47. Slow talker, ramp up the speed)
- Reading: VPN vs Proxy (2016, How to Geek)
- Video: Using Web Proxy Servers (2012, Eli the Computer Guy, 40:19)
- Reading: Forward Proxy vs Reverse Proxy (Best answer 2016, Stackoverflow)
- Video: Understand Proxy/Firewall/NAT/PAT Traffic Flows (2014, Laura Chappell. 13:33. Heads up, assumes you know what things like demultiplex means.)
Tor’s Special Sauce
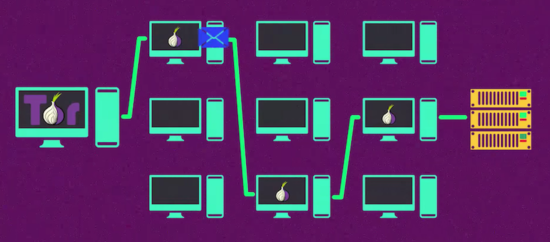
The Tor network bounces your requests through a series of proxies via a special protocol called Onion Routing. Each computer only knows about the one before and the one after. It only takes three hops for originator to become obscured. Onion routing is not just sequential call forwarding. Each new node peels off a layer of encryption, only then discovering who it should send the message on to. Only the exit node will see the original data packet.
- Video: What is Tor and Should You Use It (2016, Mashable, 2:24)
- Reading: Tor Is For Everyone: Why You Should Use Tor (2014, EFF)
- Interactive InfoGraphic: Tor and HTTPS (EFF)
- Video: How Tor Works – A ComputeCycle Deep Dive (2012, ComputerCycle 10:10. Actually talks about session keys)
- Video: Onion Routing and TOR Overview | Mechanics (2013, SourceFire, 9:44 and 12:59)
- Reading: Tor Overview Page (Tor Project)
Tor isn’t magic
All security products fail. Security is a process. Learning about the shortcomings of Tor can fail without writing the whole attempt off completely seems like the most grownup choice. It’s also kind of fascinating lesson in secure system design.
- Video: Security concerns with Tor (2013, Eli the Computer Guy, 29:12. Fair warning, he’s anti-Tor, btw. Says he wouldn’t use it, but gives no alternatives.)
- Video: How Tor Users Got Caught (2015, Garrett Fogerlie, 34:46)
- Reading: Is Tor still secure after Silk Road? (2015, Phys.org)
- Reading: Has the Tor network really been compromised? (2015, Quora, 2nd answer by Shava Nerad also came highly recommended.)
- Reading: Mozilla and Tor release urgent update for Firefox 0-day under active attack (2016, ArsTechnica, Windows users only)
- Reading: Court Docs Show a University Helped FBI Bust Silk Road 2, Child Porn Suspects (2015, Motherboard)
- Video: Tor: Hidden Services and Deanonymisation [31c3] (2015, CCCen)
- After Dec. 2016, things have gotten more complicated legally.
- The FBI’s Quiet Plan to Begin Mass Hacking (2016, TorProject)
- DOJ insist rule 41 change not important (2016, TechDirt)
- Expanded Government Hacking Powers Need Accompanying Safeguards (2016, EFF)
Ways to Support Tor
The Tor project valiantly maintains one of the very best band-aids we’ve got for the fact that the internet was not designed to address privacy concerns at it’s core. Like with VPNs, if one understands what the tool is for, it’s invaluable to have available. Help the Tor project by going ahead and sending your innocuous data traffic over it, and by setting up a relay node to mitigate that demand. Exit nodes require a deeper level of commitment, but you can donate to support one. If Tor traffic becomes popular and common place, more ISPs and server companies will get comfortable with it and the onion routing protocol in general.
- Tor Project Download Page
- Reading: Tor Browser for Windows (2016, Security in a Box)
- Reading: 5 Ways to Stay Safe From Bad Tor Exit Nodes (2015, Make Use Of)
- Reading: 11 Do’s and Don’ts of Tor Network (Hongkiat, no date displayed)
- Reading: Donate to Relay Provider via TorProject FAQ
- Reading: How you can make Tor faster for $10 a month (2016, Motherboard)
- Reading: EFF Tor Challenge (original start 2014, EFF)
- Reading: Support the Tor Project 2016 (2016, TorProject)
- Resources: Educational Outreach Materials (2015, TorProject)
Making Tor Obsolete
Folks involved in the Tor project work very hard to make folks safe on the internet as it exists now. But what if the internet was designed completely differently? Although flawed, some of the nascent “Tor alternatives” explore P2P architectures. Look into conversations around the Future Internet. Tools like OpenFlow. provide the ability to rapidly prototype network architecture. Blockchains may not just be for Bitcoin anymore. Have a research group with its own ideas? Submit a proposal. If this topic tickles your nose try checking out MIT OpenCourseWare 6.033 Computer System Engineering.
I hope this post pointed you in the direction of helpful resources to understand how Tor works, where it fits in the privacy tool box, and how to properly connect to the network. Tor’s had some struggles, but it’s in good hands.


Pingback: One Thing To Do Today: Who decides what you know?